DSL syntax: security store
The scripts that you can use with the SecurityControl feature to update the security store are formatted according to a domain-specific language (DSL). You can use the script builders provided in the APIs to create a script to update the security store. However, if you want to create the script by some other method, ensure that it conforms to the DSL.
Note: You should stop the server before editing the security store directly.
If you are using a cluster, all the servers in the cluster should be stopped before editing.
If the server or cluster is running, changes should be made using the management console or the API.
The following sections each describe the syntax for a single line of the script file.
Note: The path keyword is synonymous with the topic keyword used in previous
releases of
Diffusion™
Cloud
. Both keywords are accepted. Prefer
path.
Assigning global permissions to a role
Railroad diagram


Backus-Naur
form
set
"
role_name
"
permissions
[
'['
global_permission
[
,
global_permission
]
']'
]
Example
set "ADMINISTRATOR" permissions [CONTROL_SERVER, VIEW_SERVER, VIEW_SECURITY, MODIFY_SECURITY] set "CLIENT_CONTROL" permissions [VIEW_SESSION, MODIFY_SESSION, REGISTER_HANDLER]
Assigning default path permissions to a role
Railroad diagram
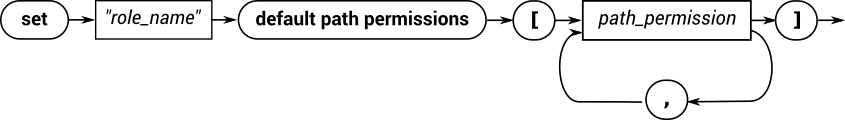

Backus-Naur
form
set
"
role_name
"
default path permissions
[
'['
path_permission
[
,
path_permission
]
']'
]
Example
set "CLIENT" default path permissions [READ_TOPIC , SEND_TO_MESSAGE_HANDLER]
Assigning path permissions associated with a specific path to a role
Backus-Naur
form
set
"
role_name
"
path
"
path
"
permissions
[
'['
path_permission
[
,
path_permission
]
']'
]
Example
set "CLIENT" path "foo/bar" permissions [READ_TOPIC, SEND_TO_MESSAGE_HANDLER] set "ADMINISTRATOR" path "foo" permissions [ MODIFY_TOPIC ] set "CLIENT_CONTROL" path "foo" permissions [ ]
Removing all path permissions associated with a specific path to a role
Railroad diagram


Backus-Naur
form
remove
"
role_name
"
permissions for path
"
path
"
Example
remove "CLIENT" permissions for path "foo/bar"
Including roles within another role
Railroad diagram


Backus-Naur
form
set
"
role_name
"
includes
[
'['
"
role_name
"
[
,
"
role_name
"
]
']'
]
Example
set "ADMINISTRATOR" includes ["CLIENT_CONTROL" , "TOPIC_CONTROL"] set "CLIENT_CONTROL" includes ["CLIENT"]
Assigning roles to a named session
Railroad diagram
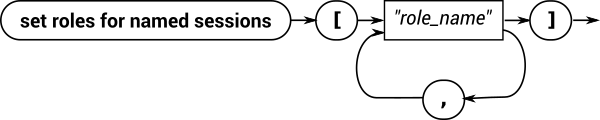

Backus-Naur
form
set roles for named sessions
[
'['
"
role_name
"
[
,
"
role_name
"
]
']'
]
Example
set roles for named sessions ["CLIENT"]
Assigning roles to an anonymous session
Railroad diagram


Backus-Naur
form
set roles for anonymous sessions
[
'['
"
role_name
"
[
,
"
role_name
"
]
']'
]
Example
set roles for anonymous sessions ["CLIENT"]
