DSL syntax: system authentication store
The scripts that you can use with the SystemAuthenticationControl feature to update the system authentication store are formatted according to a domain-specific language (DSL). You can use the script builders provided in the APIs to create a script to update the system authentication store. However, if you want to create the script by some other method, ensure that it conforms to the DSL.
The following sections each describe the syntax for a single line of the file.
Adding a principal
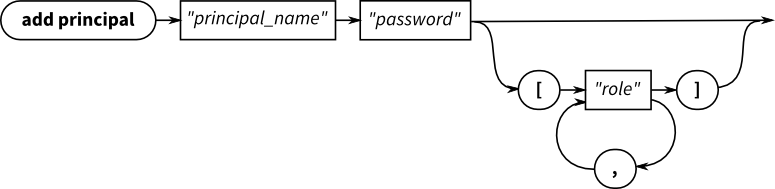
add principal "user6" "passw0rd" add principal "user13" "passw0rd" ["CLIENT", "TOPIC_CONTROL"]
The password is passed in as plain text, but is stored in the system authentication store as a secure hash.
Removing a principal

remove principal "user25"
Assigning roles to a principal

assign roles "agent77" ["CLIENT", "CLIENT_CONTROL"]
When you use this command to assign roles to a principal, it overwrites any existing roles assigned to that principal. Ensure that all the roles you want the principal to have are listed in the command.
Setting the password for a principal

set password "user1" "passw0rd"
The password is passed in as plain text, but is stored in the system authentication store as a secure hash.
Verifying the password for a principal

verify password "user1" "passw0rd"
The password is passed in as plain text, but is stored in the system authentication store as a secure hash.
Allowing anonymous connections
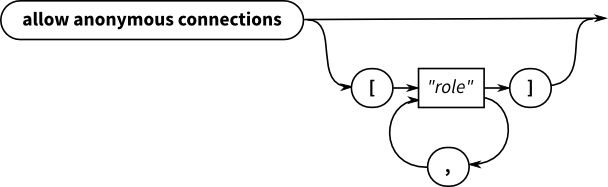
allow anonymous connections [ "CLIENT" ]
Denying anonymous connections

deny anonymous connections
Abstaining from providing a decision about anonymous connections

abstain anonymous connections
This page last modified: 2019/11/22